Syslog Tutorial
: How It Works, Examples, Best Practices and More

Syslog is a standard for sending and receiving notification messages, in a particular format, from various network devices. Messages include timestamps, event messages, severity, host IP addresses, diagnostics, and more. In terms of its built-in severity level, it can communicate a range between level 0, an emergency, level 5, a warning, unstable system, critical, and level 6 and 7 that are informative and debugging.
In addition, Syslog is open. Syslog was designed to monitor network devices and systems to send notification messages if there are any problems with the operation; It also sends alerts for previously notified events and monitors suspicious activity through the change log/event log of participating network devices.
The Syslog protocol was initially written by Eric Allman and is defined in RFC 3164. Messages are sent over IP networks to event message collectors or syslog servers. Syslog uses User Datagram Protocol (UDP), port 514, to communicate. Although, syslog servers do not return an acknowledgment of receipt of messages. Since 2009, syslog has been standardized by the IETF in RFC 5424.
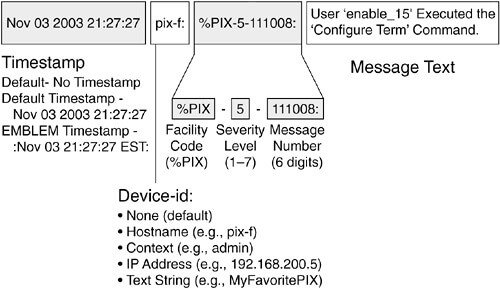
Screenshot via Flylib
Today, it
has gained wide support on many operating systems, including almost all versions of Linux, Unix, and MacOS. For Microsoft Windows, Syslog is supported through open source and third-party commercial libraries.
In the
simplest definition, registration is the act of keeping a record. System administrators have engaged in an ongoing debate about what level of detail to record their system data. There is the disadvantage between using disk space too fast and not having enough data in your logs.
However, the
benefits of logging are still extensive, especially when fixing the code problem. It is necessary to have a standardized and centralized system to generate, record and record messages. In addition, it helps improve your ability to control and use log data. Here are some other benefits:
Reduce the number of problem tickets
- Reduce
- downtime
- Decrease the volume of business interruptions
- Promote preventive troubleshooting
Without logging, it can become a nightmare to search for a single transaction that may have been processed on any of your servers. With centralized logging, you get a correlated view of all log data. Conversely, reviewing each log file separately can take quite some time. This is why using syslog to forward local log messages to a remote log analysis server has become the standard for logging solutions.
Syslog Server Components
You now understand how Syslog provides a central repository for logs from multiple sources. To achieve this goal, syslog servers have several components, including
: A syslog listener
- : The listener collects and processes syslog data sent over UDP port 514. Although, there is no acknowledgment receipt and messages are not guaranteed to arrive.
- A database-syslog server needs databases to store massive amounts of data for quick access.
- Management and filtering software: Since there can be huge amounts of data, it can take too long to find specific registry entries. The syslog server needs help automating the work, as well as filtering to see the specified log messages. To illustrate, you can extract messages based on specific parameters, such as a critical event or device name. You can also use the filter to avoid seeing certain types of entries through the Negative Filter rule. If desired, you can display all critical log messages from a firewall.
How it works
There are three different layers within the Syslog standard, which are:
Syslog content (
- information contained in an event message
- generates, interprets, routes and stores
- Syslog transport (transmits messages)
) Syslog application (
messages)
In addition, applications can be configured to send messages to multiple destinations. There are also alarms that give instant notifications for events such as:
- Hardware errors
- Application failures
- Lost contact
- Incorrect
configuration
In addition, alarms can be set to send notifications via SMS, pop-up messages, email, HTTP and more. Since the process is automated, the IT team will receive immediate notifications that there is a sudden failure of any of the devices. (Image via Wikimedia Commons)
Syslog
servers
Syslog servers are used to send diagnostic and monitoring data. Data can be analyzed for system monitoring, network maintenance, and more. Since the Syslog protocol is supported by a wide range of devices, they can conveniently log information to the Syslog server.
SNMP data can be used to quickly assess any point of failure. Syslog servers can also have automated events to trigger alerts that help prevent downtime or outages. Here is a list of some Windows-based syslog servers:
1. Kiwi Syslog server. This server is easy to install and generates reports in plain text or HTML. The software handles Syslog and SNMP, even from Linux and UNIX hosts. It is compatible with Win XP
32/64, Win 2003 32/64, Windows Vista 32/64, Win7 32/64, Windows 2008 R2 32/64, Windows 8, Windows Server 2012 and 2012 R2.
2. PRTG. This adds a sensor to PRTG monitoring to enable Syslog capability. It focuses on SNMP and Syslog protocol data. It supports any 64-bit Windows environment running Windows Server 2012 R2.
3. SNMPSoft Sys-log Watcher. This is a dedicated syslog server for a wide variety of devices. You can also analyze and manage non-standard syslog. It is compatible with Windows XP through Windows 10.
4. The Dude. This system is used for general network management with a built-in syslog server. In addition, it comes with functionality for remote registration through the RouterOS. It is compatible with Windows 2000 or later. However, it also runs on Linux or MacOS using Wine/Darwine.
5. Visual Syslog Server. This is a lighter syslog option that analyzes alerts in real time. Thresholds can be configured to trigger scripts and programs. It is compatible with Windows XP, Vista, 7, 8, 8.1, as well as Windows Server 2003, 2008, 2012.
6. Datagram. This program offers enterprise-grade functionality. Works well in large environments. Gets and stores data from Syslog. In addition, it is compatible with Windows 2000 and later versions.
For Mac OS X, you can use Splunk, which allows system monitoring and syslog events. In fact, Splunk is known as the tool for operational intelligence. In addition, you can configure Splunk as a forwarder to your central monitoring server. To configure Mac OS X Syslogd:
1. Open a Terminal 2 window
. Back up syslogd.conf in the /tmp folder by typing
$cp /etc/syslog.conf /tmp/syslog.conf.bkp
3. Open the configuration file in the editor of your choice
$ sudo vi /etc/syslog.conf
Password: The ‘sudo’ command is used to run vi with root privileges.
4. Replace the IP address 192.168.1.12 with the IP address if the network interface of your Splunk 5 server.
Type ‘i’ in vi to enter insertion mode (text input). Be sure to use tabs and no spaces between the picker and action fields.
6. Save and exit. Save the file
by typing ‘:wq <enter>’
7 Restart the ‘syslogd’ service and test it by typing
$ ps -e | grep syslogd 5070 ?? 2:33.75 /usr/sbin/syslogd
Here are the commands that restart the service
: $ sudo launchctl unload /System/Library/LaunchDaemons/com.apple.syslogd.plist $ sudo launchctl load /System/Library/LaunchDaemons/com.apple.syslogd.plist
To log an event, open a new Terminal window and type:
$ logger -s -p user.info Splunk test syslog forwarding
The format
syslog Syslog has a standard log message definition and format defined by RFC 5424. As a result, it consists of a header, structured data (SD), and a message. Within the header, you will see a description of the type, such as:
- Priority
- Timestamp
- Application
- hostname
- Process
- Message ID
version
ID
Then, you’ll see structured data that has blocks of data in the format “key = value” enclosed in square brackets. After the SD, you will see the detailed log message, which is encoded in UTF-8.
For example,
the following message: <34>1 2003-10-11T22:14:15.003Z mymachine.example.com your – ID47 – BOM’su root’ failed for lonvick on /dev/pts/8
It corresponds to the following format:
<PRIORITY>VERSION ISOTIMESTAMP HOSTNAME APPLICATION PID MESSAGEID STRUCTURED DATA MSG
Syslog messages Syslog
messages
are used to report emergency levels and warnings regarding software or hardware problems. To illustrate, a system restart will be sent through the warning level. A recharge of the system will be sent through the information level. If debugging commands are generated, they are transmitted through the debug level.
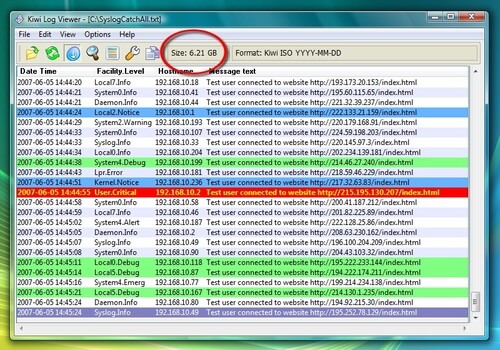
Screenshot via Cisco
These are the message levels of Syslog
: Emergency messages: the
- system is unavailable and cannot be used (could be a “panic” condition due to a natural disaster) Alert messages:
- Action should be taken immediately (an example is the loss of backup ISP connection)
- Critical messages: critical conditions (this could be a loss of the primary ISP connection
- must be resolved within a specified period of time
- warning conditions (indicates that an error may occur if no action is taken) Notification messages
- : things are normal, but still an important condition (immediate action usually not required
- Informational messages: informational messages (for reporting and measurements
- : Debugging-level messages (provides information about debugging applications)
) Error messages: error conditions (
) Warning messages:
)
) Message debugging
Here are some additional examples from TechZone. This system error message
: May 11 10:40:48 scrooge disk-health-nurse[26783]: [ID 702911 user.error] m:SY-mon-full-500 c:H: partition maintenance measures for /var were not enough – still using 96% of partition space
It can be divided into the following columns
: Column 1 = “May 11 10:40:48” > Timestamp Column 2 = “scrooge” > Loghost Column 3 = “disk-health-nurse[26783]: ” > Application/Process Column 4 = “[ID 702911 user.error]” > Syslog facility.level Column 5 = “m: SY-mon-full-500” > Message ID Column 6 = “c:H : partition health…” > Message [possibly including rid, sid, ip] And,
here’s an example of a summary message
: May 11 10:00:39 scrooge SG_child[808]: [ID 748625 user.info] m:WR-SG-SUMMARY c:X vhost:iscrooge61.seclutions.com:80 (http) GET/=> http://bali/ , status:200 , redirect URL:<n/a> , referer:<n/a> , mapping:bali , request size: 421, backend response size: 12960, audit token:- , Time statistics (microseconds): [Total requests 16617, allow/deny filters 1290, backend responsiveness 11845, Response processing 1643, ICAP reqmod <n/a>, ICAP respmod <n/a> ] Timestamp: [2012-05-11 10:00:39] [ rid:T6zHJ38AAAEAAAo2BCwAAAMk sid:910e5dd02df49434d0db9b445ebba975 ip:172.18.61.2 ]
Containing the following columns:
Column 1 = “May 11 10:00:39” > Timestamp Column 2 = “scrooge” > Loghost Column 3 = “SG_child[808]:” > Application/Process Column 4 = “[ID 748625 user.info]” > Syslog facility.level Column 5 = “m:WR-SG-SUMMARY” > Message ID Column 6 = “c:X vhost:…” > Message [including time and RID, SID, IP statistics] The
most important log files to track and monitor
Monitoring log files are critical because they help you manage any errors in the operation of your operating system. Some types of relevant information you will receive include:
- User issues
- Security breaches
- Hard drive failures or power outages
Of course, there are high-priority log files that you should always keep track of. Log files include
: /var/log/messages-Contains most system messages /var/log/secure-Authentication messages /var/log/
- cron-Logs Job activities
- maillog-Mail transactions
- var/log/
- messages
cron /var/log/
If you were to search in /
, you would find:
The
- timestamp
- host name of the running program
- Name of the utility that caused the message
- The action that took place
The
Pros
and Cons of Syslog
A troublesome scenario is when your /var/log/messages file gets crowded due to incorrect registry settings. Also, there will be times when your system registry will cause unforeseen problems. That’s why it’s imperative to understand how to control your registry and where your records are kept. Also, there may be some packet loss if there is a large burst of network traffic.
Also, the fact that Syslog is UDP-based means that there can be issues with reliability. On the other hand, as systems become more complex, it becomes increasingly important to collect and monitor all relevant data produced by applications.
This data can be analyzed to determine how systems behave. In addition, logs are considered a reliable data source for understanding current system statistics and making trend predictions. Not to mention, logs are used for activities like troubleshooting or rolling back the system after a failure accident.
Best practices
In terms of protecting your log files, you’ll have plenty of devices to generate that data. Still, it’s considered best practice to funnel all of your log data to a dedicated host that’s protected and hardened.
Also, you just want to open the syslog port on all firewalls between you and the UDP/514. If you have a geographic network, you must have a local registration host, at each location, that sends data to the central registration host.
You can also rotate a log file once it reaches a certain size. However, the UNIX logrotate utility will continue to write the log information to a new file after you rotate the old file. Here are the keys to use:
/usr/sbin/logrotate-The command logrotate /etc/cron.daily/logrotate-The shell script that runs the logrotate command daily. /etc/logrotate.conf-This
- is used as log rotation for all log entries in this
- logrotate.conf
file /etc/logrotate.d-For individual packages To rotate one log file per 1KB, use logrotate.conf under $cat
/tmp/output.log { size
1k
create 700 bullet bullet rotate 4 }
Gives you three options
:
- size 1k-logrotate only runs if the file size is equal to or greater than this size create-rotate the
- create a new file with users, groups, and permissions set
- rotate: this keeps only the four most recent
original file and
rotated log files With an increasing number of organizations moving to the cloud, the need for records management tools and services has never been greater. It’s good to have centralized records, but you also need the right tools to analyze them effectively. Going through the files individually will drive you crazy. Here are several free and paid tools:
1. Retrace: One of Stackify’s development tools and the only development tool that combines APM, bugs, metrics, and logging monitoring to provide a fully integrated multi-environment tool that gives you application performance superpowers.
2. Loggly – This is a cloud-based management and analytics service provider that has a free and paid plan starting at $49 per month. With its dynamic field explorer, you get a bird’s-eye view of your logs. It also comes with powerful full-text searches.
3. GoAccess: This is a terminal-based log analyzer that allows you to view real-time web server statistics. It is also open source and free to use. In addition, it is available on Github.
4. logz.io: This tool has both free and paid plans starting at $89 per month. It has a Kibana-powered interface that allows you to easily search through millions of records. You can also filter your results with custom parameters.
5. Splunk – This is a popular tool that has been around since 2003. It also comes in both free and paid plans. The price of the paid plan depends on the amount of volume you process. Plus, it comes with powerful breakdowns that allow you to go back in time with ad-hoc queries.
6. Logstash: This is a free open source tool for managing and collecting your events and logs. Also, you can use it together with Kibana.
7. AWStats: This free analytics tool has a community of thousands of users. This is because it allows you to generate optimized reports as well as export log data in different formats for offline analysis. Moreover, you can run it on almost all popular platforms.
8. Deep Log Analyzer: This tool can analyze log files created by IIS and even Apache web server. The user-friendly interface allows you to generate custom reports. You can also export analyzed data in HTML or Excel format.
9. BareTail: With this tool, you can analyze and read real-time information. You can also connect to a remote web server. If you need to jump to a specific point, you can do it right away.
For a list of 51 useful records management tools, check out our list here. And please visit this list of other helpful resources to get started with
Syslog: Syslog
- Log Tutorial Better Understanding
- : Servers, Messages, and Security Description
- Syslog Conf – Specific Log Types/Tags Guidance Configuring
- a server
Logging on Linux Understanding Syslog
of
Centralized Linux logging Syslog is a widely used tool that makes managing complex networks much simpler. Also, with the right tools, you don’t have to worry about the volume of data as you can filter easily and conveniently.
