In this chapter, we will learn how to use the Wi-Fi cracking tools that Kali Linux has incorporated. However, it is important that the wireless card has a supported monitoring mode.
Fern Wifi
Cracker Fern Wifi
cracker is one of the tools that Kali has to crack wireless
.
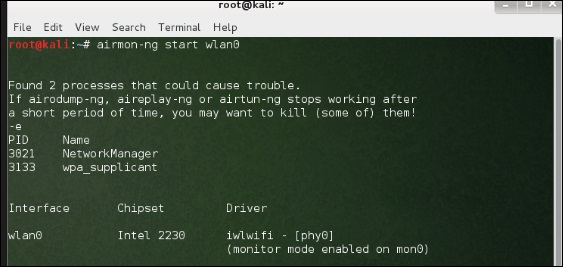
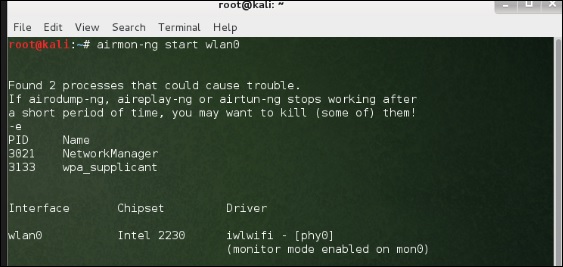
Before opening Fern, we need to convert the wireless card into monitoring mode. To do this, type “airmon-ng start wlan-0″ in the terminal.
 Now, open Fern Wireless Cracker. Step
Now, open Fern Wireless Cracker. Step
1 – Applications → Click on “Wireless Attacks” → “
Fern Wireless Cracker”. <img src="https://www.tutorialspoint.com/kali_linux/images/fern_wireless_cracker.jpg" alt="
Fern Wireless Cracker
” />
Step 2 − Select the wireless card as shown in the screenshot below.
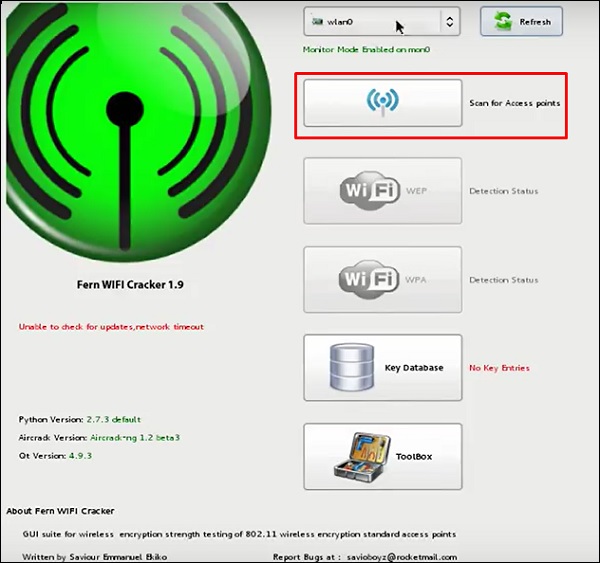
 Step
Step
3 − Click “Search for Access Points
“. 
Step 4 – After finishing the scan, it will display all found wireless networks. In this case, only “WPA networks” were found.
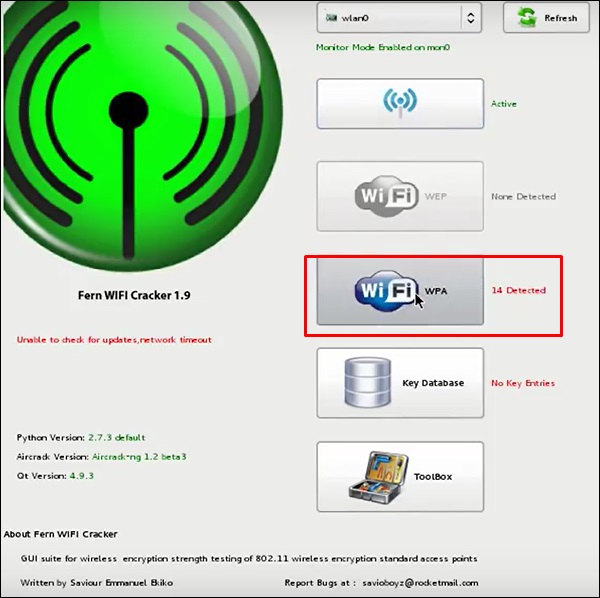
Step 5 − Click WPA Networks as shown in the screenshot above. Displays all wireless found. Generally, in WPA networks, it performs dictionary attacks as such.
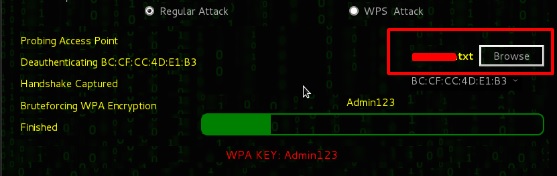
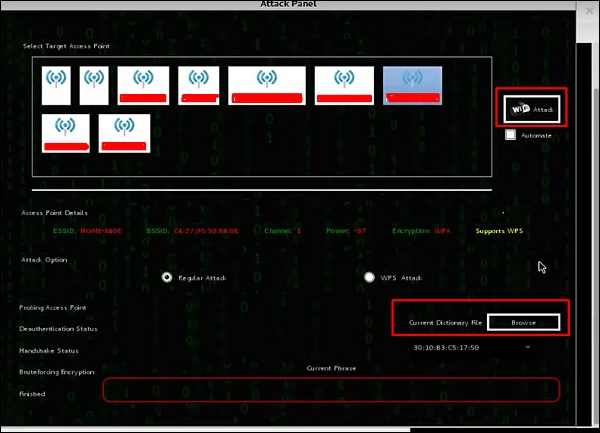
Step 6 – Click on “Browse” and find the list of words to use for the attack.
 Step
Step
7 − Click “Wi-Fi attack”.
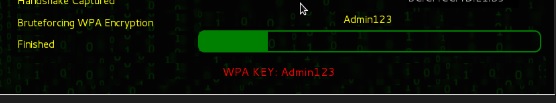
Step 8 – After finishing the dictionary attack, it found the password and it will be displayed as shown in the following screenshot image.
 Kismet
Kismet
Kismet
is a WIFI network analysis tool. It is a layer 2 802.11 wireless network detector, sniffer and intrusion detection system. It will work with any wireless card that supports raw monitoring mode (rfmon) and can sniff out 802.11a/b/g/n traffic. It identifies networks by collecting packets and also hidden networks.
To use it, convert the wireless card into monitoring mode and to do this, type “airmon-ng start wlan-0″ in the terminal.
Let’s learn how to use this tool.
Step
1 – To launch it, open the terminal and type “kismet
“. 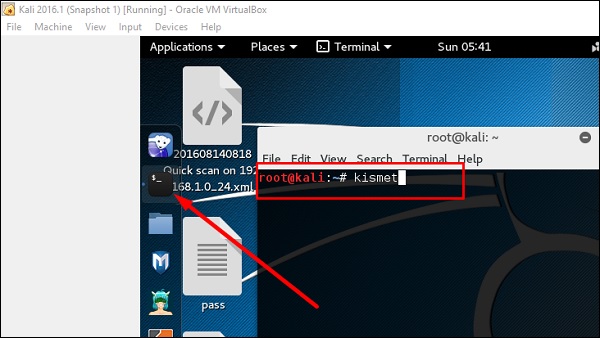 Step
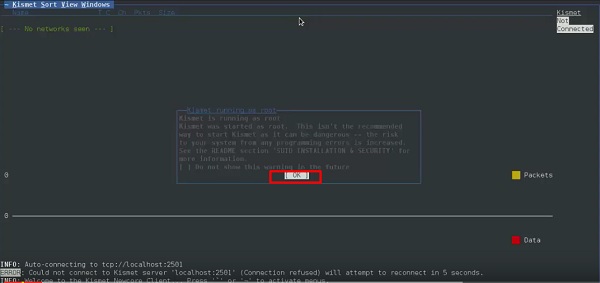
Step
2 − Click “OK”.
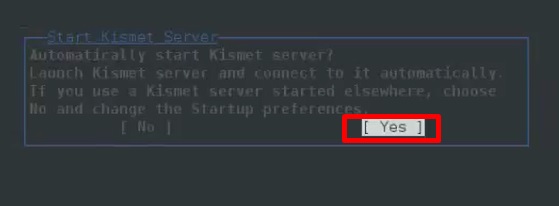
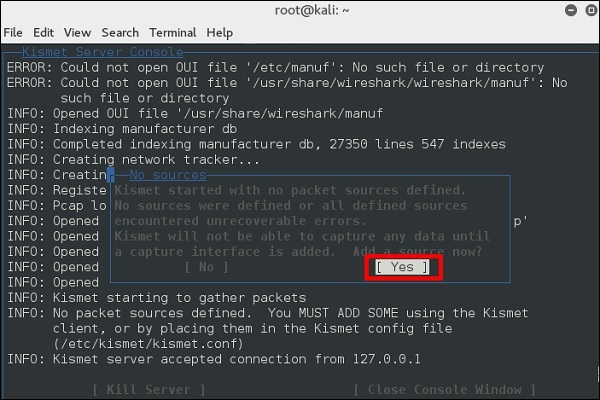
Step 3 − Click “Yes” when prompted to start Kismet Server. Otherwise, it will stop working.
Step 4 − Startup options, leave as default. Click “Start”.
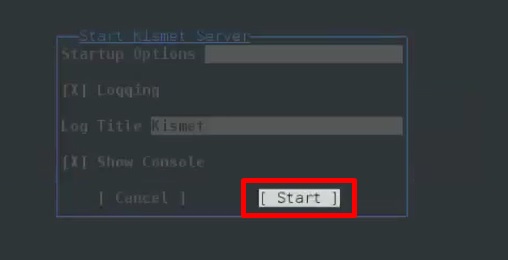
Step 5 − It will now display a table asking you to define the wireless card. In this case, click Yes.
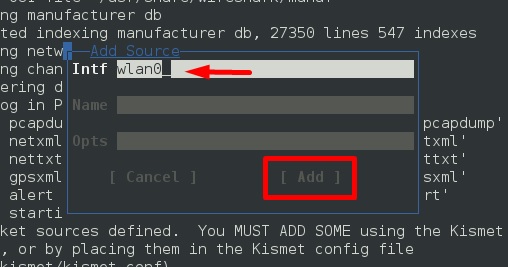
Step 6 − In this case, the wireless source is “wlan0”. It will have to be typed in the “Intf” section → click “Add”.
 Step
Step
7 − It will start sniffing wifi networks
as shown in the screenshot below. 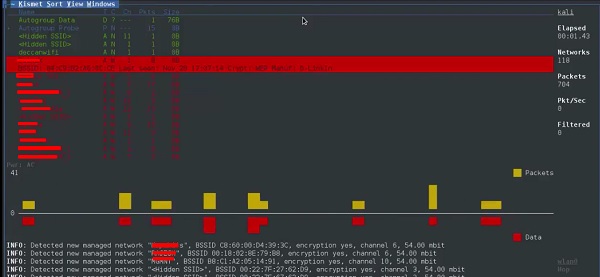
Step 8 − Click on any network, produce the wireless details as shown in the following screenshot.
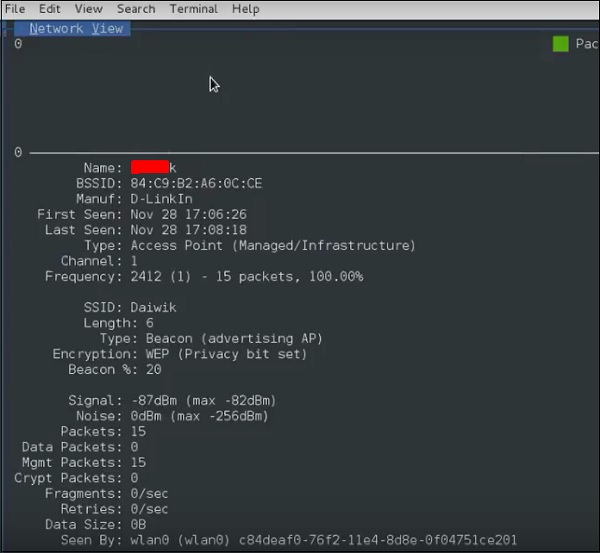
GISKismet
GISKismet is a wireless visualization tool to represent the data collected using Kismet in a practical way. GISKismet stores the information in a database so that we can query data and generate graphs using SQL. GISKismet currently uses SQLite for database and GoogleEarth/KML files for graphics.
Let’s learn how to use this tool.
Step 1 – To open GISKismet, go to: Applications → Click on “Wireless Attacks” → giskismet.

As you will recall in the previous section, we used the Kismet tool to explore data about wireless networks and all these Kismet data packets in
netXML files.
Step 2 – To import this file to Giskismet, type “root@kali:~# giskismet -x Kismetfilename.netxml” and it will start importing the files.
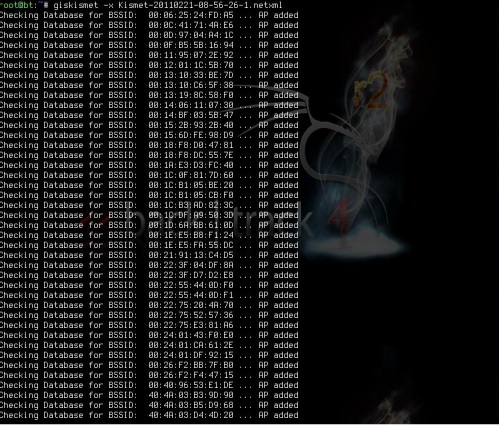
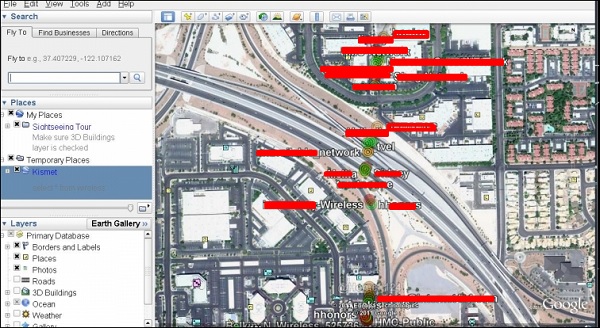
Once imported, we can import them into Google Earth the Hotspots we found before
.
Step 3 – Assuming we have already installed Google Earth, we click File → Open file that Giskismet created → Click “Open”.
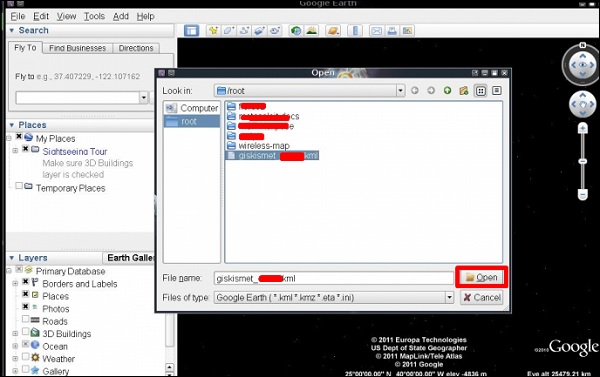
The following map will be displayed.
 Ghost Phisher Ghost Phisher
Ghost Phisher Ghost Phisher
is a popular tool that helps create fake wireless access points and then create Man-in-The-Middle-Attack.
Step
1 – To open it, click on Applications → wireless attacks → “phantom phishing”.
<img src="https://www.tutorialspoint.com/kali_linux/images/ghost_phisher.jpg" alt="
Ghost Phisher
” />
Step 2 − After opening it, we will set up the fake AP using the following details.
- Wireless interface input: wlan0
- SSID: Wireless AP name
- AP
- will have WAP: Password that this SSID will have to connect
IP address: IP that the
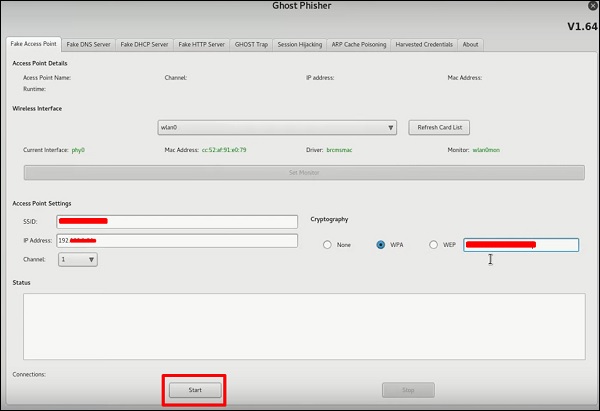
Step 3 – Click the Start button
. Wifite
is another wireless clacking tool, which attacks multiple WEP, WPA, and WPS encrypted networks in a row
.
First of all, the wireless card has to be in the monitoring mode
. Step
1 – To open it, go to Applications → Wireless Attack →
Wifite.  Step 2 − Type “
Step 2 − Type “
wifite
-showb” to search for the networks. <img src="https://www.tutorialspoint.com/kali_linux/images/wifite_showb.jpg" alt="
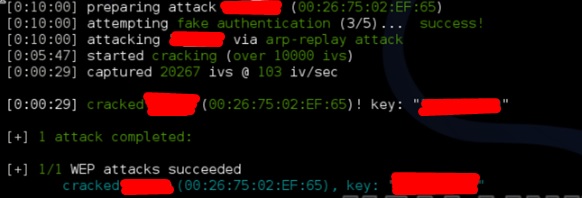
Wifite Showb” /> 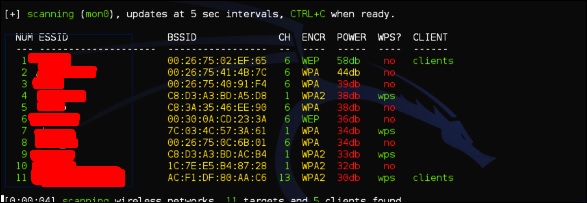 Step 3 − To start attacking wireless networks, click Ctrl + C. Step 4 – Type “1”
Step 3 − To start attacking wireless networks, click Ctrl + C. Step 4 – Type “1”
to decrypt the First Wireless Connection.
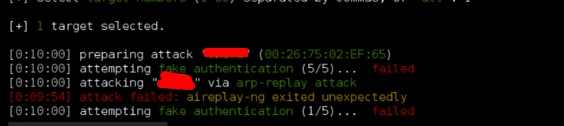
Step 5 − Once the attack is complete, the key will be found.